About Us
We at Endpointsecurity.in help buissnesses maximize the value of their technology by providing them with the most advanced security tools available in the market.
- Range of products to suit everyone from a budding startup to a big conglomerate
- Best in-class technologies at appropriate price
- Fast and efficient customer support for all the products
Ranging from mobile to cloud products, we offer the tools to make your technological enviroment safe from cyber threats growing in our technologically advancing world. We aim to reduce the risk of cyber attacks and protect your organisation against the unauthorised exploitation of systems, networks and technologies. No other company delivers as broad and deep a spectrum of cyber security to buissnesses around the world.
Learn More
To keep up with the ever evolving security products and security threats
NGFW and UTM
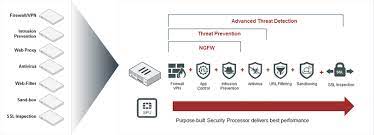
There really aren’t any differences in a UTM and a NGFW. The technologies used in the two are essentially the same, and they generally have the same capabilities. UTM devices are typically classified with lower throughput ratings than their NGFW counterparts, but for all practical purposes the differences are in marketing.
The reason for the name shift is that there was a pervasive line of thought stating a device
capable of all of the functions of a UTM/NGFW would never be fast enough to run in an enterprise
network.
As hardware has progressed, the capability of these devices to hit multi-gigabit speeds
began to prove that they were indeed capable of enterprise deployment. Rather than try and fight
the sentiment that a UTM could never fit into an enterprise, the NGFW was born.
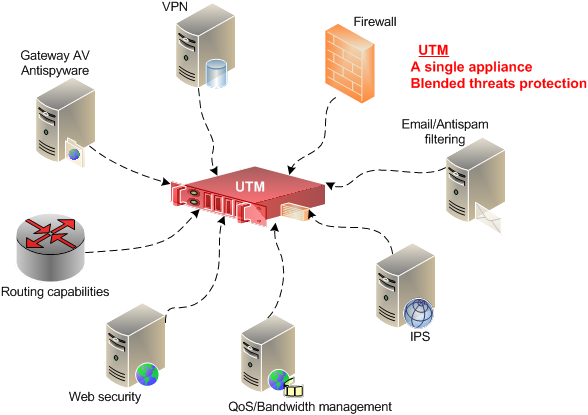
Internet filter
Internet filtering restricts or controls the content a user is capable to access. Internet filtering can be an excellent tool to help prevent attacks or loss of security. It can also help in increasing the productivity of users
Data Loss Protection
Data loss prevention reduces the risk of sensitive data leaking outside the company. It detects potential data breaches/data ex-filtration transmissions and prevents them by monitoring, detecting and blocking sensitive data while in use.
Email protection
Email protection is used by scanning every email attachment to protect the company from attacks, such as phishing.

Request a Demo
Explore the key features and capabilities of best-in-class solutions provided by companies leading the forefront of cybersecurity with a demo.

Submit query
To report a problem or to get support from our executives please submit your query and relevent information.
Contact Us
endpointsecurity.in
Providing best in class products and services for buissness with cybersecurity needs. Ranging from mobile to cloud products, we offer the tools to make your technological enviroment safe from cyber threats growing in our technologically advancing world.
info@example.com
+1 5589 55488 55s




.svg.png)








