CrowdStrike's cloud-native next-gen antivirus protects against all types of attacks from commodity malware to sophisticated attacks — even when offline.
Falcon Prevent is fully operational in seconds, no need for signatures, fine-tuning, or costly infrastructure.
From initial deployment through ongoing day-to-day use, Falcon Prevent operates without impacting resources or productivity.
Falcon X: Automated Threat Intelligence
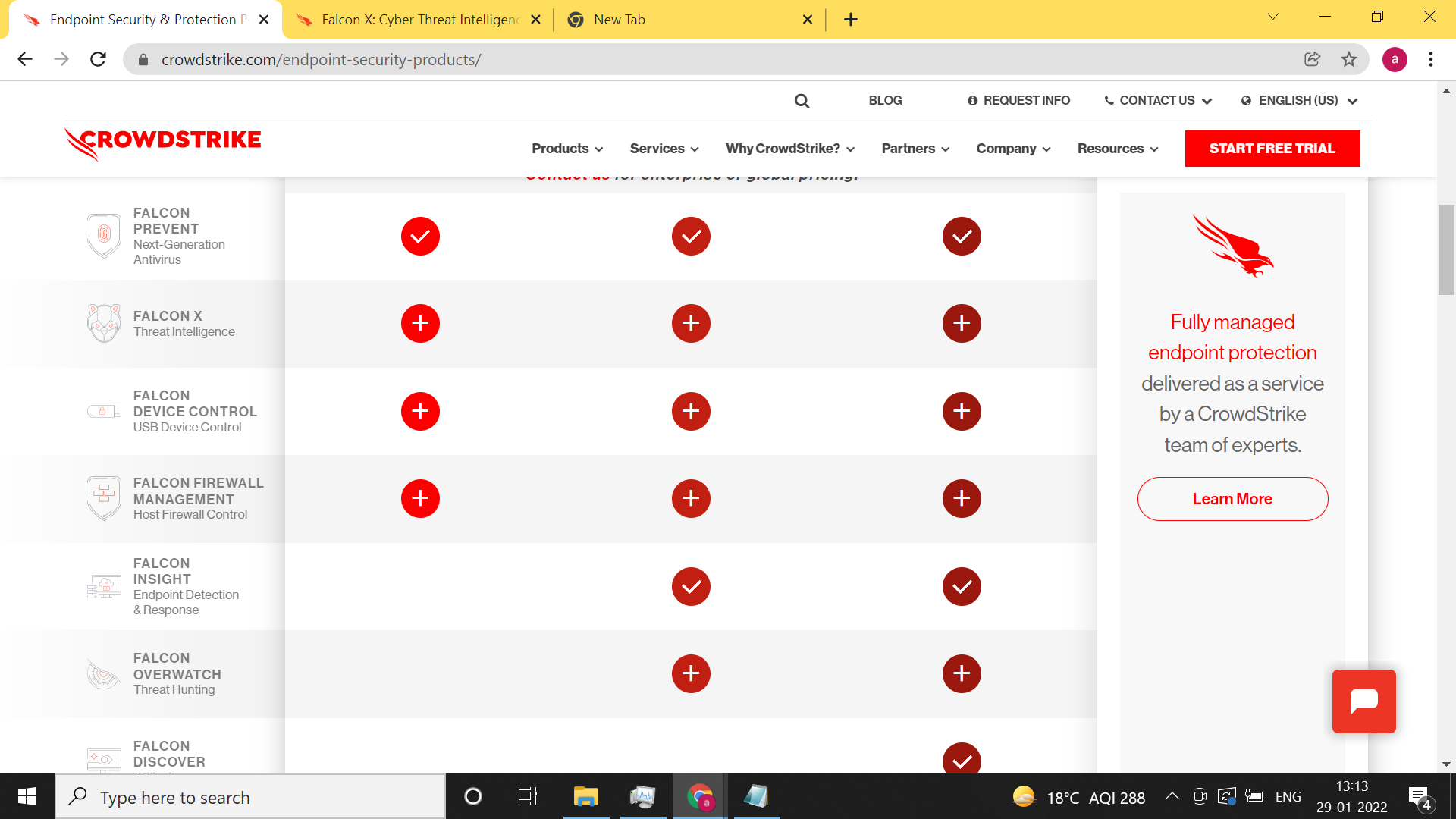
The Falcon Platform is flexible and extensible when it comes to meeting your endpoint security needs. You can purchase the bundles or any of the modules listed below. The additional modules can be added to Falcon Endpoint Protection bundles.
Stand-alone modules can be purchased by anyone and do not require a Falcon Endpoint Protection bundle. Our specialized products are for customers working with more stringent compliance or operational requirements.
- Falcon spotlight
- Falcon for mobile
- falcon Forensics
Additional Falcon modules
- Falcon Search engine
- Falcon Sandbox
Stand-alone modules
Falcon spotlight
-
UNIFIED THREAT AND VULNERABILITY MANAGEMENT:-
As part of an integrated platform that prevents exploits and post-exploit activity, Falcon Spotlight™ allows you to research common vulnerabilities and exposures (CVEs) to examine threat actor profiles and targets. -
SCANLESS AND FAST:-
Spotlight utilizes scanless technology, delivering an always-on, automated vulnerability management solution with prioritized data in real time. It eliminates bulky, dated reports with its fast, intuitive dashboard. -
ZERO IMPACT:-
The cloud-native CrowdStrike Falcon® platform and single lightweight agent collect data once and reuse it many times. As a result, Spotlight requires no additional agents, hardware, scanners or credentials — simply turn on and go.
Falcon For Mobile
-
AUTOMATED THREAT PROTECTION:-
Falcon for Mobile prevents phishing attempts, identifies vulnerable devices, and detects malicious and unwanted activity on business-critical mobile apps -
COMPREHENSIVE VISIBILITY:-
Gain insight and enable mobile threat hunting with real-time visibility into app activity to help eliminate mobile malware and the risk of silent failure -
EXTEND EDR TO MOBILE DEVICES:-
Protect your mobile devices with the Falcon Platform that can also secure your workstations, servers, cloud workloads, identities and data.
Falcon Forensics
-
SIMPLIFY FORENSIC DATA COLLECTION AND ANALYSIS:-
Falcon Forensics offers comprehensive data collection while performing triage analysis during an investigation. Forensic security often entails lengthy searches with numerous tools. Simplify your collection and analysis to one solution to speed triage. -
ACCELERATE TRIAGE ANALYSIS WITH PRESET DASHBOARDS:-
incident responders can respond faster to investigations, conduct compromise assessments along with threat hunting and monitoring with Falcon Forensics. Pre-built dashboards, easy search, and view data capabilities empower analysts to search vast amounts of data, including historical artifacts, quickly. -
SPEED RESPONSE TIME AND HONE IN ON ATTACKER ACTIVITY:-
Falcon Forensics automates data collection and provides detailed information around an incident. Responders can tap into full threat context without lengthy queries or full disk image collections.
Falcon Search Engine
A SEARCH ENGINE FOR CYBERSECURITY
Organizations can now search for all types of malware — both metadata and binary content — and get results from the Falcon platform in seconds. Combining fast and comprehensive malware search with CrowdStrike Falcon Intelligence™ gives Security Operations Center (SOC) analysts and threat researchers the advantage they need to stay ahead of the adversary.
Falcon SandBox
Falcon Sandbox performs deep analysis of evasive and unknown threats, enriches the results with threat intelligence and delivers actionable indicators of compromise (IOCs), enabling your security team to better understand sophisticated malware attacks and strengthen their defenses.
-
Detect Unknown Threats:-
Unique hybrid analysis technology detects unknown and zero-day exploits while defeating evasive malware. -
Achieve Complete Visibility:-
Uncover the full attack lifecycle with in-depth insight into all file, network, memory and process activity. -
Respond Faster:-
Save time and make all security teams more effective with easy-to-understand reports, actionable IOCs and seamless integration.
